Device Handling and Digital Evidence Processing and Analysis
Using Predefined Criteria
This protocol will cover all the steps needed to comply with the attached court order in case # FMCE13007297 signed by Judge Fabienne Fahnestock. Specifically, the defined protocol encompasses all the steps taken from the onset of the collection until case reporting if requested and each area below is described in detail.
- Collection
- Acquisition/Imaging
- Analysis
- Reporting
Collection
Prior to moving the storage device or data source such as a hard drive, mobile device, cloud data, social media accounts or another form of digital data, proper documentation of the collection process will be documented and/or photographed.
- Create a historical record of personnel access, condition and location of the storage device or data source . Document the transfer of the evidence from location to location or person to person in a chain-of-custody form approved by the Law Firm or Attorney.
- Connections: storage device or data source s, such as USB, microSD, SD cards, GPS Units, CD/DVDs, hard drives, GPS units, mobile devices, smart watches, etc. shall be connected to a laptop or another device capable of imaging the storage device or data source or cloud based data. In civil cases where the device itself will be returned to the owner(s) and will be used after the imaging, live acquisitions using collection devices such as a USB drive with imaging software will be the preferred method vs taking the device apart and removing the storage drive or media.
- To preserve the current state of the storage device or data source , avoid unnecessary usage of the storage device or data source while being imaged. Do not:
- Manually search the device using non-forensics tools or techniques
- Use or click 3rd-party applications or installed applications on the device itself
- Attempt to unlock/lock unless it is required for accessing and imaging
- Apply power to the device unless it is required for accessing and imaging
- Be aware of and cautious while handling Mobile storage devices or data source with touch screens and side buttons.
- To avoid pressing buttons, handle the storage device or data source by the corners or with care to avoid inadvertent device actions.
- The side buttons may be customizable and may have been changed by the owner. Assumptions cannot be made about the intended purpose of a particular button.
- If applicable, use a power source while imaging the storage device or data source to prevent powering off during the collection process.
- Prior to imaging a mobile device, verify the device is not connected to WiFi, Bluetooth, Cellular or GPS to eliminate all incoming and outgoing data transmissions or potential data changes.
- If applicable, locate the “auto-lock” or “screen timeout”, set to “never” or the maximum time allowed to prevent the device from locking during imaging .
- Document or notify the device custodian or owner of any changes that are made to the original configuration of the storage device or data source in order for them to choose to reset them after the imaging process.
Acquisition/Imaging
Imaging is the process of creating a forensic copy and/or snapshot-image and/or logical collection of files/folders and/or cloud based data such as social media or cloud services including WhatsApp, iCloud, Google, Microsoft, Mi Cloud, Huawei, Samsung, E-Mail (IMAP) Servers and more. Prior to performing the acquisition process it is necessary to have a signed court order or consent to search from a person with consent authority.
- Search Warrant: A search warrant is a judicial order issued by a judge or magistrate that gives permission and authorizes the Law Firm, Attorney’s or Cyber Forensics to conduct a search a storage device or data source .
- Consent to Search: Only a signed consent to search form obtained from the owner or custodian is needed to Acquire/Image the device.
- During the Acquisition/Imaging steps, personnel shall:
- Ensure the destination storage media is forensically clean or digitally sterile of any previously stored data, by conducting a forensics process called “wiping” on the source media.
- Upon formatting the drive an encrypted volume using Veracrypt or another encryption program, shall be used to protect the data if the data is to be shipped or placed in an area which could accidentally cause it to be stolen or lost.
- Format the wiped and encrypted volume storage location/media using the Windows extended File Allocation Table (exFAT).
- Create a folder on the
forensically clean storage media with a unique name relative to the
matter but do not use titles which do not identify, in part, the
originating source or case name/number; two examples are listed
below:
2020_2_10_devicename/model_forensicimagename_1TB or
Case1234567_Aaron.vs.Baron_MacBook.
Information which can be included are:
- Device owner name and/or case number
- Device name/model (evidence and/or serial number, if possible)
- Extracted data name/type (Hard drive, USB, Cloud, Facebook, WhatsApp, etc
- Data source size either logical, physical or indicated
- Evidence item number
- Address of the where the data was collected
Execute the forensics tool/software (FTK Imager Lite, Oxygen Detective, Magnet Axiom, etc) to acquire or image the storage device or data source and complete the imaging process.
- During the initial acquisition/imaging process, the tool/software will allow for the inclusion of a unique signature or “digital fingerprint” of the extracted data and/or image file. This unique signature is called a hash signature. If applicable to the matter, at minimum, the examiner shall obtain a MD5 hash value for the data acquired.
- Once completed, verify the acquisition/image is readable and accessible by forensics software.
Analysis
Utilize appropriate software/tools in accordance with training and/or certification. During analysis data filtering can be applied if mandated by the court or if mutual agreements are approved.
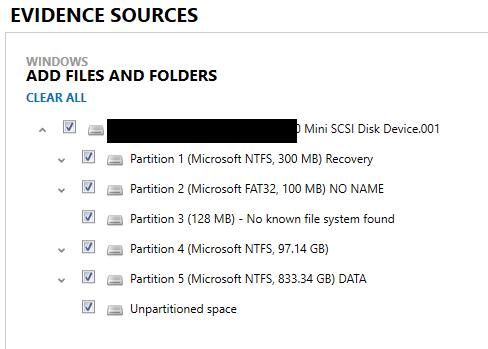
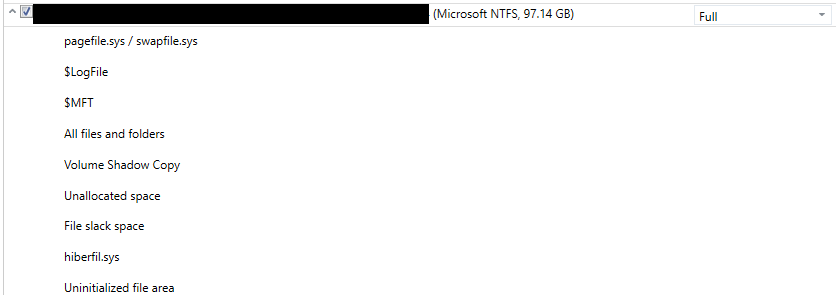
The analysis will include all areas which contain deleted or non-deleted data and all data types using court order criteria listed below. As an example, a computer search will include all the below areas of a hard drive in a Windows environment:
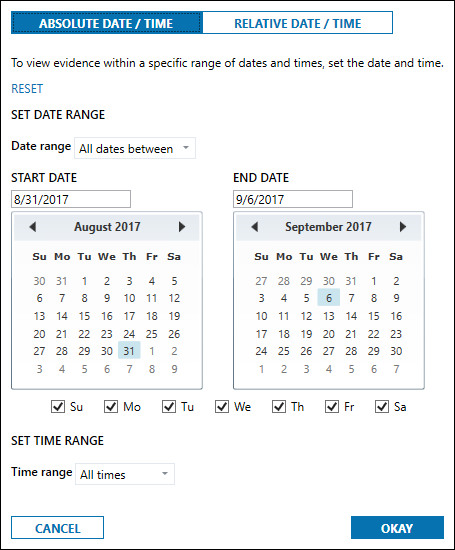
- When filtering data using date and
time criteria, the analysis will be conducted with a defined date and time
range. Specifically, in this case the date and time range known as the Relevant
Time Period is:
- Any search of the Former Wife’s devices is limited to the time period from August 31, 2017 – September 6, 2017, except as set forth in Paragraph 5 herein. This time period is reflected below as the actual setting to be utilized within the forensics software:
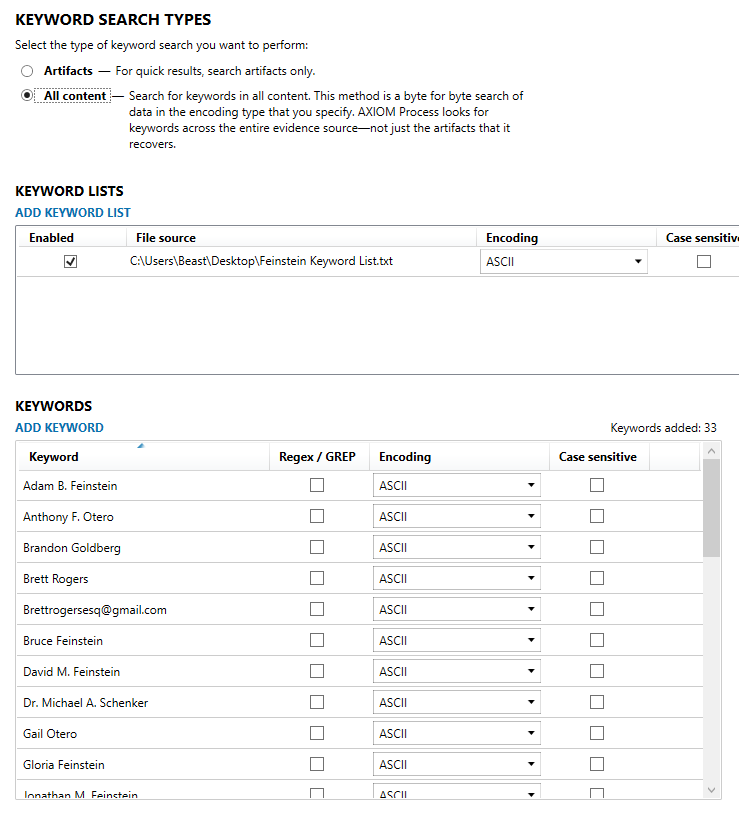
- Filtering evidence based on keywords
or keyword lists. You can stack keywords or keyword lists to refine your
results even further. Once keywords or keyword lists are added to the analysis
process, those lists and keywords appear as filtering options. The search terms to be used to further filter
data based on the above Relevant Time Period will be:
- Stacy Sarnoff
- Terry Fixel
- Rae Chorowski
- Miranda Soto
- Miranda Lundeen Soto
- Miranda Lundeen
- Miranda L. Soto
- Lyle Feinstein
- [email protected];
- [email protected];
- [email protected];
- [email protected]
- [email protected]
- Shook Hardy & Bacon (any variation thereof)
- Adam B. Feinstein
- David M. Feinstein
- Jonathan M. Feinstein
- Private investigator
- CaseNo: FMCE13007297
- Page 2 of 7
- Anthony F. Otero
- Gail Otero
- Top-Notch Investigations, Inc.
- [email protected]
- [email protected]
- Brandon Goldberg (if another one of the Search Terms delineated herein is included)
- Dr. Michael A. Schenker
- Martha Jacobson
- Monica Salgueiro
- Bruce Feinstein
- Gloria Feinstein
- Michael B. Gilden
- Supportive relationship
- Brett Rogers
- [email protected]
Reporting
Reporting can be verbal and/or written and/or in a format requested by the Court, Law Firm or Attorney, or the client.