Threading: A Serious Threat for 2019
This has become a serious threat and will define 2019 for sure. Already seen it in 5 separate cyber forensics examinations and investigations:
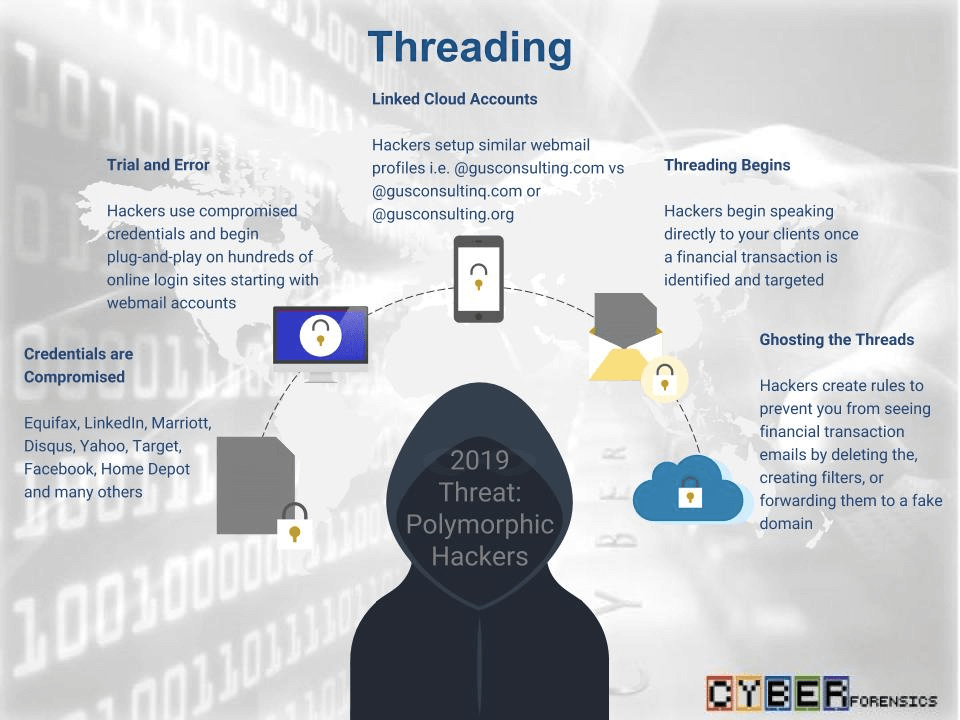
I have been conducting cyber forensics since 1996 and each year the trends set by hackers are measured by the techniques they use to steal information, money and credentials. My 2018 data breach forensics revealed a trend which shows hackers have become aggressive. Specifically, a term I coined to identify the latest hacker technique is called Threading.
Threading Case Study #1: As a result of the highly publicized breaches of LinkedIn, Equifax, Marriott and Disqus, credentials including email addresses, phone numbers, addresses, social media profiles, usernames, and passwords have been leaked. Once the data is available to hackers, they utilize the information and begin the process of plugging in credentials on various banking sites, email hosts, cloud storage and other online domains. In the old days (2016-2018) once hackers gained access to your data or systems they would steal your data or encrypt the data and then provide extortion payment information for decryption. In 2019, hackers have become polymorphic and adapted to a style of Threading which integrates themselves into your conversations and more importantly waited patiently for a pending wire or online payment transaction before taking collusive actions. Forensic examinations on separate Threading fraud cases have revealed the patience hackers are now demonstrating. Once they gain access into your email account as an example, hackers analyze your data and make themselves capable of injecting themselves into conversations and direct responses. Then begins the offensive actions which include setting up mail forwarding, creating rules such as deleting messages with certain keywords such as wire, and assuming your online identity without taking over the account. In reality, the real user is still continuing normal email communications but the ones which involve financial transactions are received but never seen.
Threading Case Study #2: Client John Doe has a consulting company call [email protected] as an example. Using credential theft described above, an effective method hackers are now using is directly receiving wires or other invoice payments by using Threading to split the conversation once the timing is appropriate. This type of Threading normally involves 3 or more parties. The party setting up the wire or payment to an invoice, the lawful recipient, and the ghost party often disguising themselves in the slightest of ways. In the domain above, [email protected], hackers will create a new domain [email protected] and begin sending Threaded emails to other trusted parties. This is done by copying an entire valid email with any related threads and pasting them into a new email and creating a forking or redirecting conversation. This very effective form of Threading has been linked to millions in losses this year and preventing hackers from would require a third party network assessment which must include phishing campaigns, cloud security assessments, and most importantly a new category of Mandatory Vulnerability changes added to the normal High, Medium, and Low Vulnerabilities.
To date, the art of Threading has defrauded law firms, real estate brokers, medical, and financial institutions and cyber forensics in each analysis all revealed evidence of Threading defined in both cases studies.
Problem: As we all transition to dedicated Cloud data storage, databases, and computing the reliance of hosted providers to offer flexibility in alerting when your Cloud space is accessed by non-validated IP addresses or anomalous ones, simultaneous accessing, rule creations, forwarding, keyword search alerts, and after hours logins, all as examples, must be offered. What should be eliminated is the ability to validate a login or emails password recovery using an email account to verify. Simply, using your mobile device to receive login codes from Multi-factor authentication must be mandatory and even though security feature has been exploited on platforms such as Outlook Web and Office 365, not implementing this simple security feature leaves your cloud door wide open.